The Belarusian intelligence service also received a demonstration of Hacking Team spyware at a 2014 law enforcement exhibition in Qatar.
Unlike most of Hacking Team’s customers, who wanted ready-made, easy-to-use remotely controlled spyware, the Belarusians had a very specific request. Rather than infecting targets with malware via the internet, they wanted to physically insert the malware and collect intercepted data via USB memory sticks, apparently to leave no record of activity that could be traced via the internet.
The request was relayed in an email from a staff member identified only as Evgeniy at Kharkiv-based Altron to Hacking Team’s Marco Bettini. Altron sells audio recording equipment for digital and analog telephone connections, as well as IP-telephony. Altron also offers GPS monitoring systems which can track moving vehicles.
Its website makes no mention of any dealings with Belarus, which has been criticized and sanctioned internationally over human rights and elections violations.
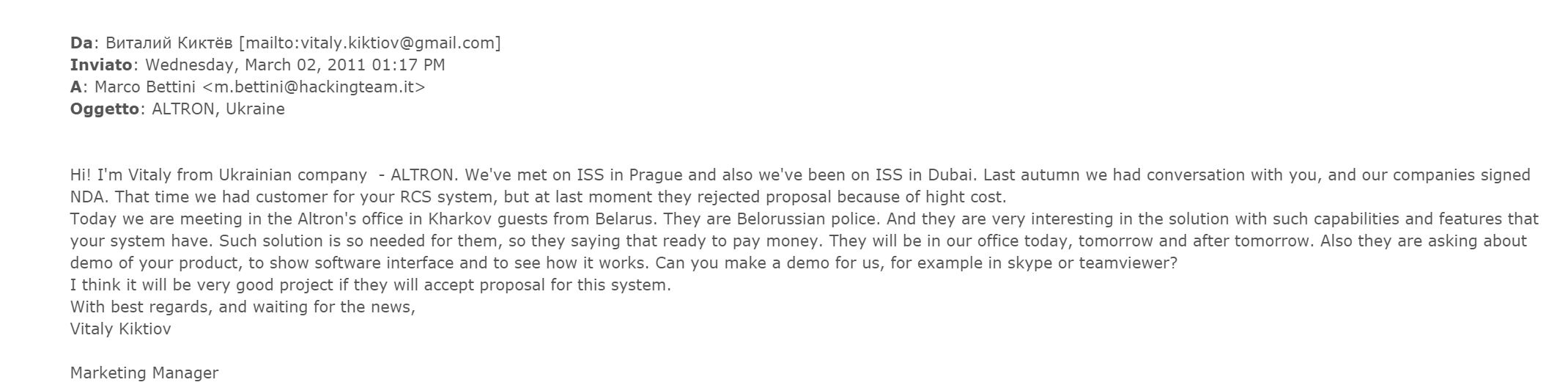
However, a 2011 email by Altron sales manager Vitaly Kiktiov to Marco Bettini from Hacking Team states, “Today we are meeting in the Altron's office in (Kharkiv) guests from Belarus. They are Belarusian police. And they are very interesting in the solution with such capabilities and features that your system have. Such solution is so needed for them, so they saying that ready to pay money. They will be in our office today, tomorrow and after tomorrow.” Hacking Team responds by sending Altron a promotional video to show to the Belarusian police, but there is no evidence a deal was made.
Read Kiktiov's conversation with Hacking Team – In Full, On Wikileaks
In 2012, the Altron staff member called Evgeniy contacts Hacking Team asking whether it would be willing to sell to an unspecified customer in Belarus despite the fact that “we heard about some EU restrictions and sanctions against Belarus.” Hacking Team never answers the question, only promising to check with its “legal department.”
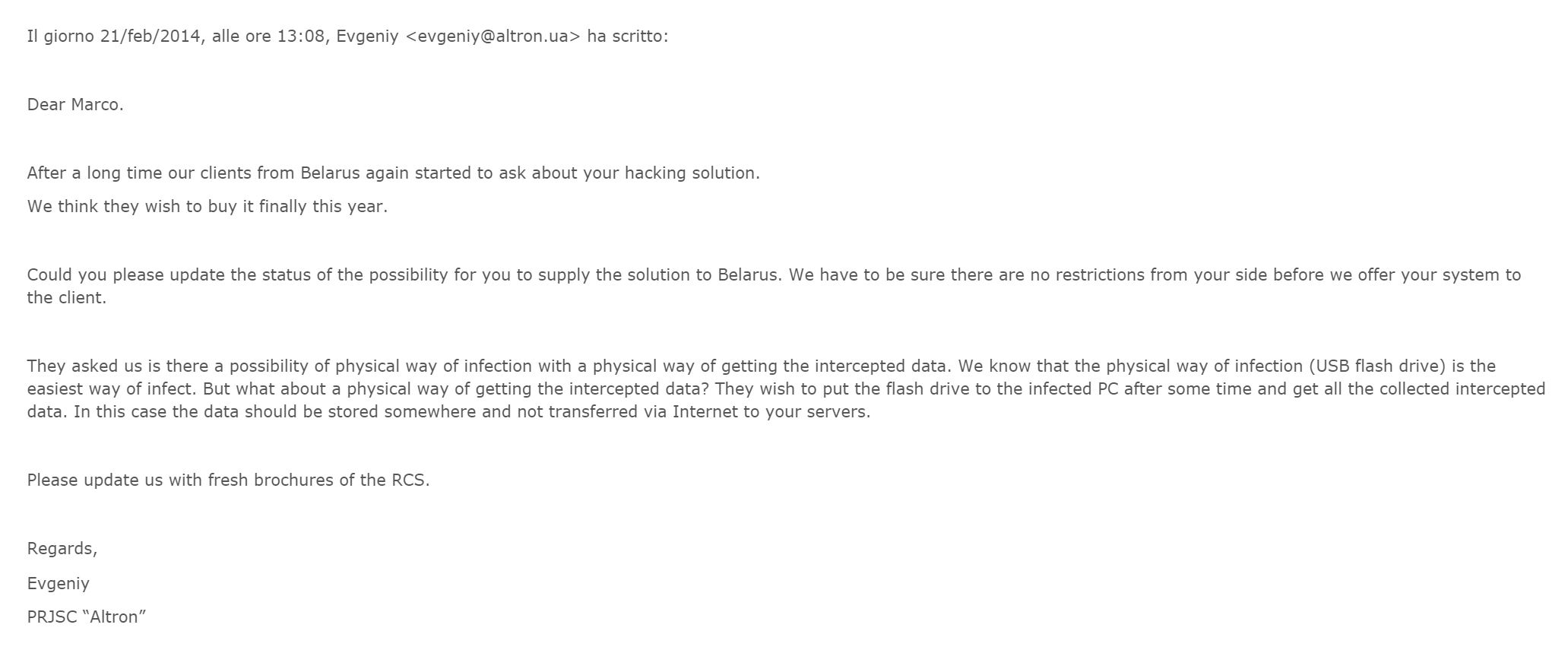
But in February 2014 Evgeniy gets back in touch, asking for an update on the legal situation and saying “after a long time our clients from Belarus again started to ask about your hacking solution. We think they wish to buy it finally this year.”
He then relays the request from Belarusian authorities about using USB flash drives rather than the internet. He writes, “They wish to put the flash drive to the infected PC after some time and get all the collected intercepted data. In this case the data should be stored somewhere and not transferred via Internet to your servers.”
Hacking Team responds saying physical infection and data removal is possible but says that any data transmitted via the internet goes straight to the client’s server, not theirs, and that hence “we never receive any data.”
Hacking Team also presses Evgeniy for details about the customer, but is only told that the “customer is one of the law enforcement agencies (government).” When Hacking Team continues asking, it is merely told “Let us ask the customer if they allow us to disclose their agency name at this stage.” Soon after, the email exchange breaks off.
The emails offer a rare glimpse into the Belarusian police surveillance methods.
Read Evgeniy’s conversation with Hacking Team – In Full, On Wikileaks
Digital human-rights-focused academic organization Citizenlab published research in February 2014 alleging that Hacking Team-related software was possibly being used by regimes in Azerbaijan, Uzbekistan and Saudi Arabia, based on the IP addresses of endpoints or servers allegedly used to transmit data online for Hacking Team’s spyware.
According to a document published by The Intercept, Belarusian intelligence also received a demonstration of Hacking Team spyware at a 2014 law enforcement exhibition in Qatar. The report lists “intelligence Belarus- Mr Alyaksey Tsymbalay” as the customer and notes that they were “very interested, they made a lot of questions.” The forms list an email address “@oac.gov.by.”
The OAC, whose full name is Operations and Analysis Center, is a little-known state agency for digital security in Belarus, and is distinct from Belarus’s main intelligence agency, the KGB. OAC was named as an “enemy of the internet” and part of the Belarusian regime’s “apparatus of repression” by Reporters Without Borders in 2013. They say the OAC “reports directly to President Alexander Lukashenko… and coordinates internet surveillance operations.”