Hacking Team insisted it did not sell its products to “repressive regimes” and “has a customer policy concerning the human rights implications of its products, and claims it investigates and may take action in response to reported cases of abuse,” according to a March 2015 report by the University of Toronto's Citizen Lab. A February 2014 report by Citizen Lab tied Hacking Team to eleven repressive regimes around the world.
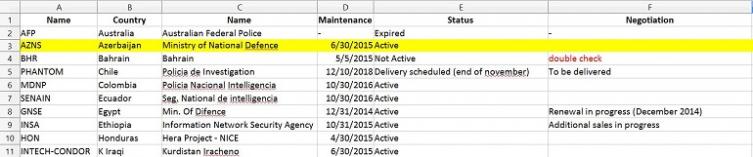
Internal company documents show Azerbaijan's Ministry of Defense purchased a license for Hacking Team's Remote Control System (RCS) surveillance spyware via a California-based intermediary called Horizon Global Group in 2013 for an initial payment of €320,000. Annual maintenance fees of €16,000 were made through Horizon in 2014 and 2015. Hacking Team could not be reached for comment.
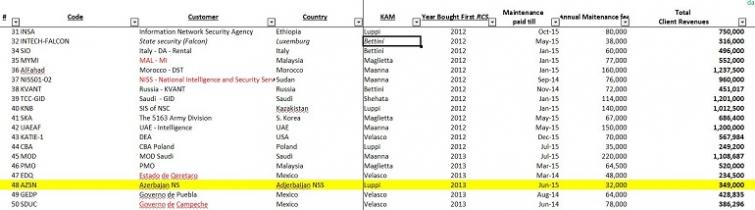
Hacking Team invoices show Horizon made payments of €130,000 on March 10, 2013 and €190,000 on May 30, 2013 for an initial RCS license. The dates and sums of these payments correspond to separate Hacking Team spreadsheets documenting payments from the government of Azerbaijan. Horizon Global Group has no online presence, public profile, or listed phone number and lists its address as “Ranchos Palos Verdes, Nevada, CA 90274”.
When contacted as part of a December 2013 investigation by the Ecuadorian newspaper El Universo, Hacking Team denied selling its products through “independent agents.”
Founded in 2003, Hacking Team describes itself as an “ethical hacking” firm specializing in “offensive IT security”. In a 2008 presentation released by Wikileaks, the company claimed its RCS software – the software it has covertly provided the Azerbaijani government since 2013 – is able to secretly “log any action performed by means of a personal computer … or smartphone.”
Remote Control System renders the use of secure communication channels moot by collecting data on an infected device itself, not only data sent over the internet. Emails are recorded by keystroke loggers before encryption and RCS can turn on a device's camera or microphone without alerting the user.
The leaked documents confirm that Hacking Team has sold RCS to the security services of Kazakhstan, Uzbekistan, Ethiopia, Turkey, Egypt, Bahrain, Russia, Sudan, and others. Of all these clients, only Russia and Sudan carry the caveat “not officially supported.”As Hacking Team has always refused to identify any of its clients publicly, the meaning of this phrase is not immediately clear.
Despite RCS's widespread use, researchers and activists have only been able to tie the governments of Sudan, UAE, Ethiopia, and Turkey to specific rights abuses involving RCS. Citizen Lab documented an RCS endpoint active in Azerbaijan from June to November 2013, but is unclear who was under surveillance.





